[HMV] Webmaster
Table of Contents
| URL | 🔗 |
|---|---|
| Level | Easy |
| Attacker IP | 10.10.10.2 |
| Target IP | 10.10.10.6 |
| Target domain | webmaster.local, webmaster.hmv |
Intro#
Today I will dig in nginx. I will start with obtaining the SSH creds using DNS records. Then I will abuse sudoable nginx to serve flags directly through the browser.
Enumeration#
Nmap#
The initial Nmap scan revealed 3 active services running on the target box, namely http, ssh and dns.
The full TCP scan didn’t find any additional open ports. Neither did the UDP scan. I started with enumerating HTTP.
HTTP#
index.html suggested there’s a password saved as TXT. The TXT could be a file, but given there was a DNS port open, this could also mean e.g. the TXT DNS entry.
 Then, I bruteforced the webserver to see if there are any files worth examining. Nothing of use though.
Then, I bruteforced the webserver to see if there are any files worth examining. Nothing of use though.
DNS#
I used dig to find out the hidden password:
It seemed the correct pair was john:Myhiddenpazzword so I used it with ssh.
SSH#
Having the foothold in place, I moved on to enumerating the machine.
/home/john#
In john’s $HOME there was a user flag and the flag.sh script:
It seemed the script could be used to obtain the root.txt contents (a.k.a. the root flag), but since I didn’t have the required permissions, it fall-backed to the user flag. But at least I confirmed that the flag is in root.txt.
Exploitation#
At this point I thought I have to exploit the flag.sh file.
I checked what am I allowed to do as john using sudo -l:
Given that I was able to run nginx I thought of writing a custom nginx.conf that would run the flag.sh script with elevated privileges and save its content in $HOME or something like that. Turns out it wasn’t necessary to abuse flag.sh, I was able to solve the challenge with nginx alone.
First I created the basic nginx.conf in /home/john:
And ran nginx:
Unfortunately going to webmaster.hmv:90 resulted in Forbidden. But I was one step closer to the finish line.
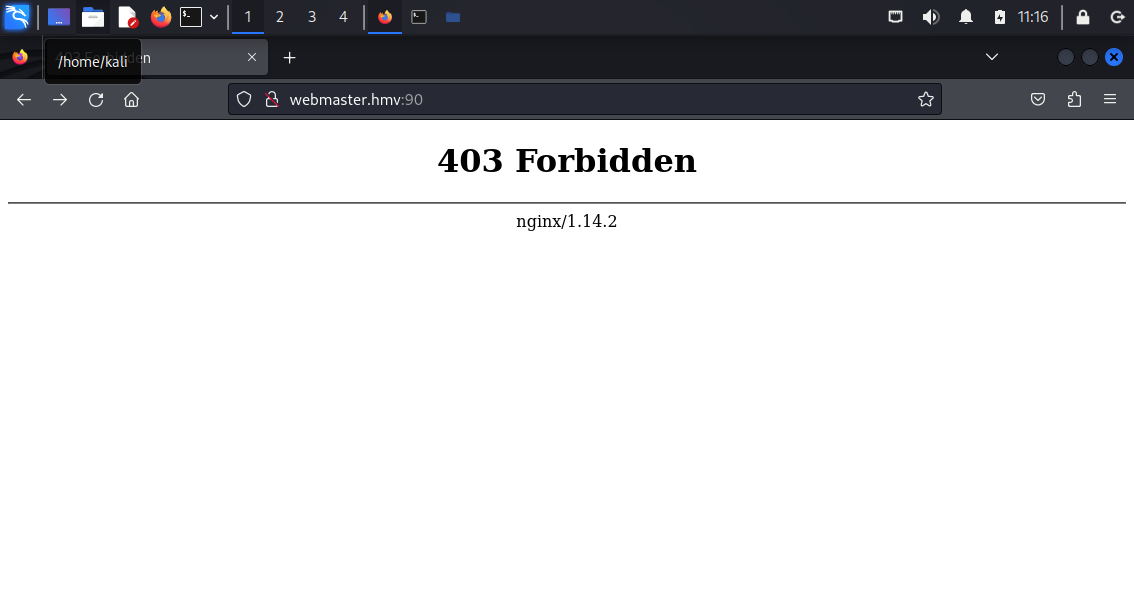
Then I thought I might be able to set the root path in nginx.conf to /root and check if I’d be able to obtain the flag this way.
To do so, I updated the configuration file to:
I still got Forbidden so after a little bit of research, I stumbled upon autoindex on option, which enabled the file browser mode:
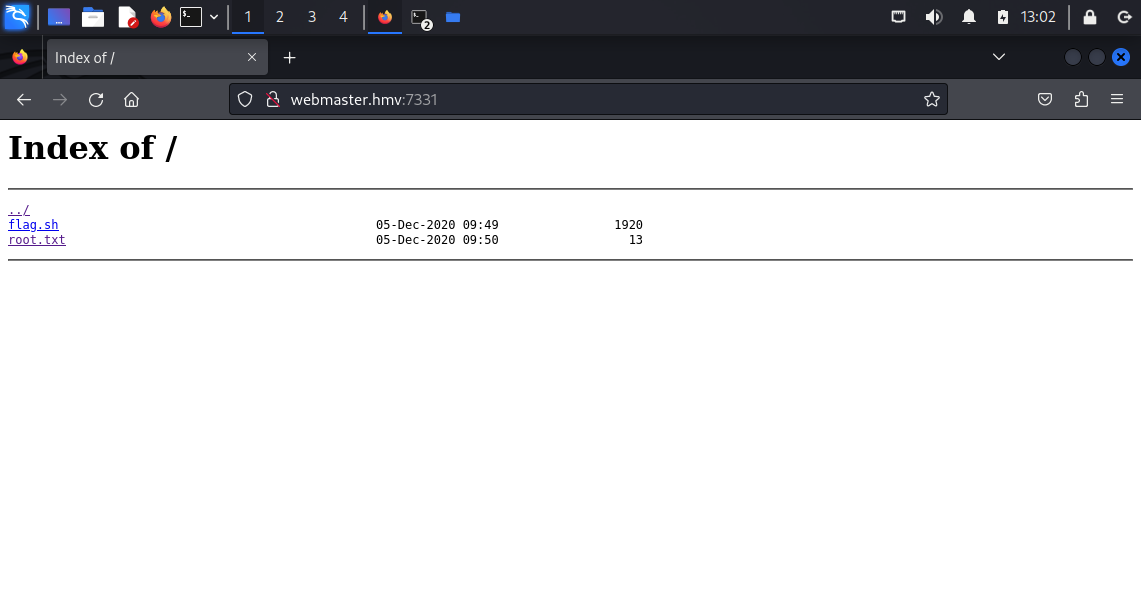
TIP: It wasn’t necessary to actually set
autoindex ontowgetthe file.
Pwned#
Pwned.