[HMV] Helium
Table of Contents
| URL | 🔗 |
|---|---|
| Level | Easy |
| Attacker IP | 10.10.10.2 |
| Target IP | 10.10.10.3 |
| Target domain | http://helium.local |
Intro#
Today I am decoding audio files. I will start with enumerating the web server and finding 2 cryptic audio files. Then I will decode the hidden password and obtain a foothold. Ultimately I will abuse ln to escalate the privileges and pwn the target.
Enumeration#
Nmap#
ssh and http with nginx 1.14.2 were open. I didn’t find anything else with -p- and -sU.
HTTP#
nginx served a very basic webpage with the relax.wav audio file attached. I downloaded it to check if there is anything hidden within later.
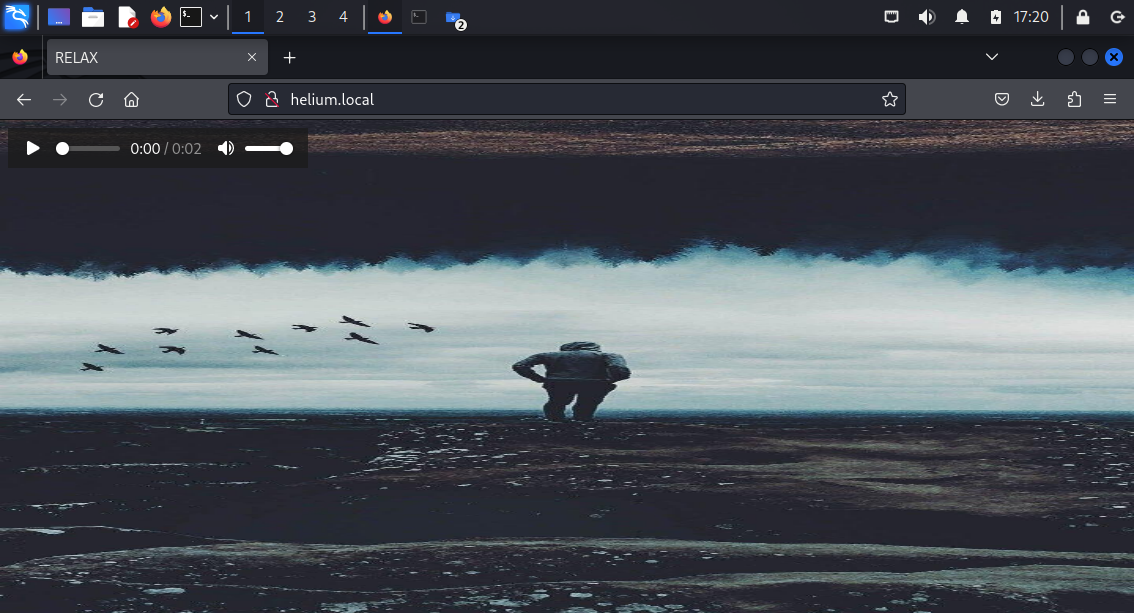
There was a comment in the source code:
Note to self: paul could be a real username on the target.
The /upload_sound route responded with:
Upload disabled (or not).
No other HTTP methods were allowed for that endpoint.
I decided to bruteforce the directory structure with feroxbuster:
Out of curiosity I checked bootstrap.min.css and it responded with:
/yay/mysecretsound.wav
From that path I was able to download yet another audio file.
audio files#
The downloaded audio files had around 0:01 of length and there was no point in listening to them. So I’ve tried strings on both.
I figured that maybe these words could be used with hydra, but before checking that, I opened the audios in Audacity and checked their spectograms. For relax.wav I found nothing, but for mysecretsound.wav there was a hidden message:
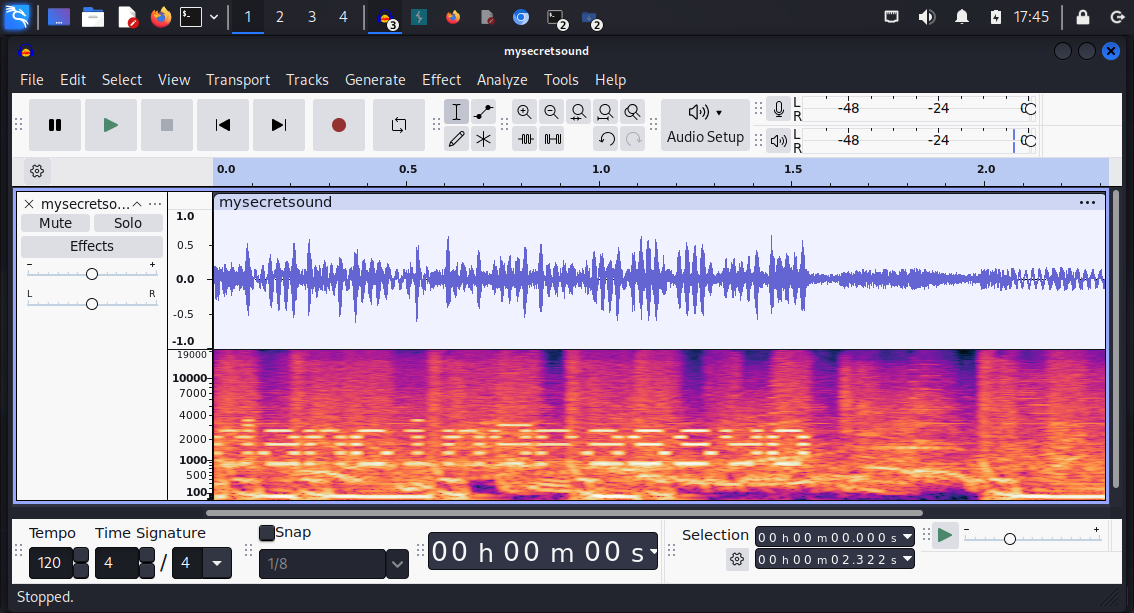
I figured this could be a password for paul, so I tried SSH.
SSH#
The foothold has been planted.
Priv Esc#
Once I logged in, I checked for sudo-able files:
ln has a known GTFObin. Supposedly it allows to escalate privileges by overwriting itself with a symlink to a shell, which, once executed, does not drop the sudo privileges. This can be done only once though. So I tried it and succeeded:
Pwned#
Pwned.