[HMV] Quick 2
Table of Contents
Enumeration#
As usual, I ran an initial scan of the target machine using Nmap to identify open ports and services.
The scan revealed two open ports:
- Port 22: SSH (
OpenSSH 8.9p1 Ubuntu 3ubuntu0.6) - Port 80: HTTP (
Apache httpd 2.4.52 on Ubuntu)
HTTP#
Upon visiting the website on port 80, I discovered a basic car maintenance company site that appeared to be a work in progress. The site was built with PHP, and the only interactive element was a “Contact Us” form.

I inspected the source code and found that all subpages were served through the index.php?page=* URL. Other than that it was a pretty ordinary code.
This led me to consider fuzzing the page parameter using gobuster to discover potential injection points.
The fuzzing revealed several interesting pages, with index.php?page=file.php in particular standing out. This indicated a potential Local File Inclusion.
Exploitation#
LFI#
I navigated to the http://target.local/file.php page and attempted to use the LFI form to include files, but it didn’t work. However, accessing http://target.local/file.php directly allowed me to exploit the LFI:
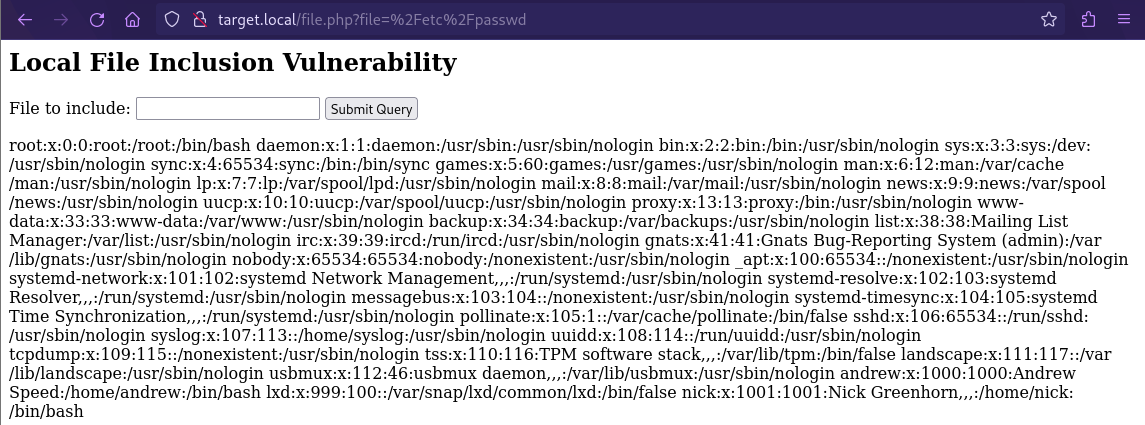
It seemed there were 2 real-life user accounts (nick and andrew, respectively) on the server.
LFI to RCE#
At this point I’ve been asking myself if I can exploit LFI to execute code remotely, although I had to research the topic first.
I stumbled upon PHP Wrappers and exploiting them to bypass read/write permissions in the target system. To confirm if they are usable, I tried:
In this case the file provided through the form gets encoded to base64 and rendered in the browser. Decoding the base64-encoded content of file.php revealed a basic LFI vulnerability script.
I then used PHP wrappers to read the contents of PHP files and crafted a PHP filter chain payload with php_filter_chain_generator to achieve RCE.
[!danger] It was crucial to use the payload directly as a
?file=parameter, not through the input, ascmdis obtained from the query parameter in this scenario.
I leveraged this payload resulting in code execution:
Bingo.
Revshell#
To open a reverse shell I started a nc session, prepared a payload of:
and sent the encoded payload as cmd=.
Immediately after getting in, I tried to access /homes of both andrews and nicks. The former wasn’t available to me, and the latter kept the user flag in /home/nick/user.txt.
Priv Esc#
Using linpeas.sh I discovered that PHP 8.1 had the capability of cap_setuid. This was my way to elevate privileges.
This successfully escalated my privileges to root.
Pwned?#
Sure.