[VH] Fristileaks 1.3
Table of Contents
| URL | https://www.vulnhub.com/entry/fristileaks-13,133/ |
|---|---|
| Level |
Intro#
Today I am hacking the Dutch informal hackers group called FristiLeaks. I’ll start with enumerating the web-service and abusing it to upload a web-then-reverse-shell, then I am going to utilise cron-enabled scripts and perl to escalate privileges both horizontally and vertically. Ultimately, I will decode the root’s password and pwn the target.
Enumeration#
Nmap#
I kicked off the reconnaissance with a basic Nmap scan to identify open ports and services on the target:
The scan revealed that only port 80 was open, running an Apache httpd server.
Meanwhile I ran full ports scan (-p-) and an UDP (-sU) scan to see if there are any other open ports. These didn’t yield any results though.
Port 80#
Upon visiting http://target.local, a webpage containing a link to x.com/tags/fristileaks and an image. There was nothing of interest here. Additionally I checked the webpage’s source code, again, to no avail.

To explore potential paths, I ran gobuster scan against the HTTP server, using the dirb/big.txt wordlist.
The /images directory listed 2 files, one of which was bassically making fun of me upfront.

Interestingly, exploring /robots.txt revealed hidden paths such as /beer, /cola, and /sisi, each displaying the same image above.
Attempting to find hidden directories using gobuster on the paths found in robots.txt did not prove useful either.
💡 Meanwhile the full Nmap scan finished and revealed a
28928port, however I didn’t know what to do about it at the time.
Ultimately I ran next gobuster scan, using rockyou.txt as a wordlist this time.
💡 Be curious
Out of curiosity I googled what
fristimeans and… well, it’s a drink.Remember the
drink fristiadvice from the homepage? Pretty effin’ ovbious.
Anyways, upon exploring /fristi, a Login Form was discovered.
Exploitation#
Inspecting the form’s source code exposed a commented-out, base64-encoded image. Might be useful later.
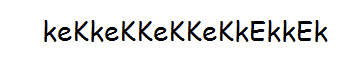
The Login Form itself made a POST request to checklogin.php upon submitting. Although I attempted the SQL injection, it proved fruitless.
However, further examination of the source code revealed something that looked like a login:
Using both the decoded image, I found the valid credentials: eezeepz:keKkeKKeKKeKkEkkEk.
Logging in allowed the uploading of files, with images being the only accepted format:

Uploading the download.png image resulted with saving the image in http://target.local/fristi/uploads/download.png:

Noice.
Webshell#
At this point I wanted to upload a webshell. The issue was the only valid files were images, so I had to embed the PHP code somehow.
Using jhead I modified the JPEG’s metadata to include a PHP webshell:
I saved as shell.php.jpg and after uploading it permitted executing commands:
http://target.local/fristi/uploads/shell.php.jpg?cmd=ls
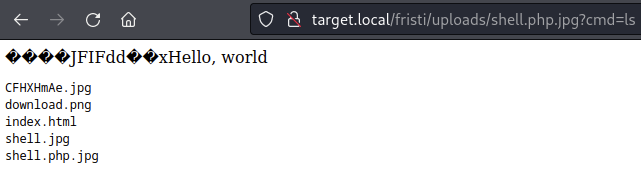
This provided access to the web server with the user apache.
❗ I will use
code-blockinstead of screenshots from now on.
Revshell#
After confirming the vulnerability, I’ve spawned the nc on port 2345 and upgraded the webshell into a reverse shell using php-reverse-shell.php:
With a stable shell, I spawned a proper PTY using python:
Now onto the privilege escalation.
Priv Esc to admin#
Exploring the /home directory revealed users admin, eezeepz, and fristigod.
Investigating /home/eezeepz, apart of a list of binaries, an interesting note was relvealed.
A note indicated restricted access but offered additional commands available from the /home/admin level.
/tmp/runthis#
Checking the /tmp/runthis script, it executed commands and stored results in /tmp/cronresult:
The script was executing the commands using the admin account, so I tried to spin another reverse shell, this time as an admin.
I’ve compared the binaries available in /usr/bin with GTFObins and found a common denominator of perl:
Perfect.
Priv Esc to root#
I listed files inside /home/admin and the whoisyourgodnow.txt looked interesting.
The contents seemed to be base64-encoded, but decoding it as is didn’t actually work.
Then I checked hte cryptpass.py file to see it encoded the given string with base64, reversed the result and then encoded it again with rot13:
Knowing that, I’ve prepared a quick decryption recipe in CyberChef:
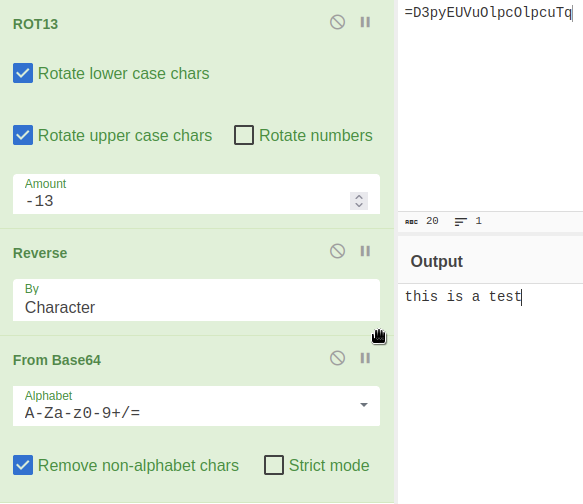
This way I decoded whoisyourgodnow.txt:
LetThereBeFristi!
and then, cryptedpass.txt:
thisisalsopw123
Now, I tried sudo -l to see what commands admin might have the access to.
This didn’t prove useful though. But hey, it’s perfectly normal to have an admin account that cannot do a thing, right?
A short while after, using ls -l, I learned that whoisyourgodnow.txt file was created by no other than fristigod. Why shouldn’t I try to log in as him?
Hello, fristigod.
Well, at least I progressed a tiny little bit.
I’ve been staring at it for a quite while, but ultimately I noticed it.
The (fristi : ALL) Moment#
I was stuck with fristigod as an username, and didn’t notice fristi is another user that should be able to execute the command!
Pwned#
Pwned.
Not sure about these 4 hours tho.